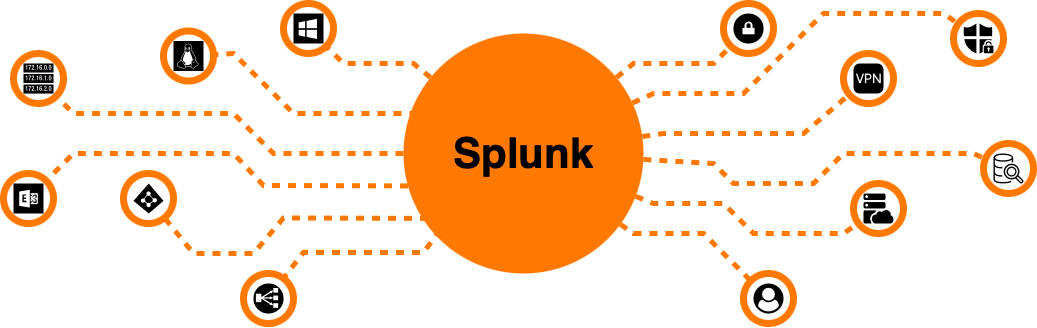
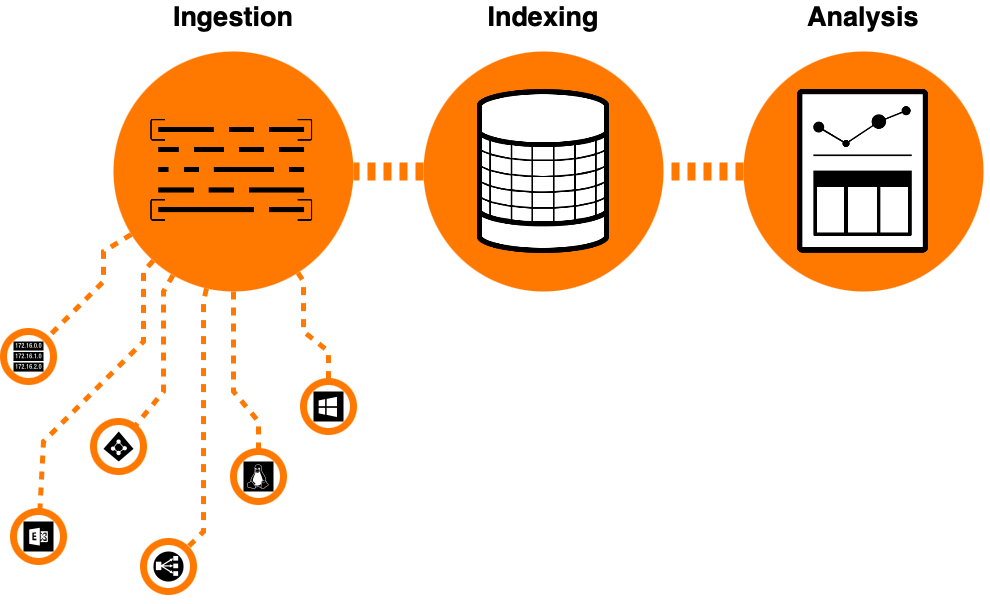
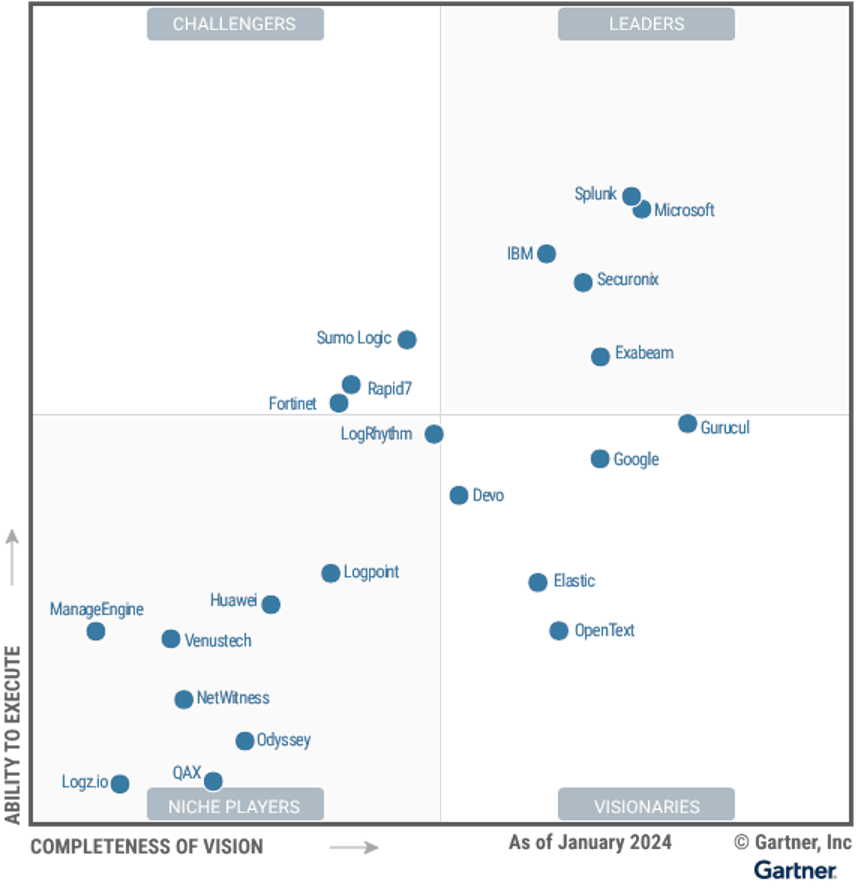
What is Splunk?
This question has been asked many times and it’s impressive how difficult it is to get a decent answer. You can spend hours on Splunk’s website going through their blogs and articles and not find a satisfying answer. Unfortunately, that is the case with most technology vendors and their websites.
Feel free to go through the Splunk article below “What does Splunk do?“ and let me know if this gives you any useful information as to what Splunk is and what it can do:
https://www.splunk.com/en_us/blog/learn/what-splunk-does.html
It is often referred to as a SIEM tool (Security Information and Event Management) or nowadays as an Observability tool, however this definition as accurate as it is, does not do it justice.
This blog is going to be my own take on answering those questions. I will avoid being vague but will also use more common day-to-day vocabulary to convey the message. Once you are done with this article, let me know how did I do?